Software mediates almost every activity, from online banking and buying to healthcare and entertainment. However, with the advancement of development in the field of software, the security threats targeting the applications have also evolved. This makes it crucial for software developers to up their game and reinforce their cyber security defenses. It requires a thorough understanding of the main threats and respective mitigation steps.
Here are ten common security threats in software development that developers must be aware of.
1. Injection Attacks
These are SQL, NoSQL, and OS command injections; they happen when an attacker sends untrusted data to the interpreter as part of a query or command. These weaknesses will provide opportunities for the attacker to execute unauthorized commands or access sensitive data. This kind of threat is among the most common security threats and mostly occurs when user inputs are properly validated, sanitized, or escaped, allowing malicious code to be executed.
Consequently, always validate and sanitize all user inputs and use parameterized queries to avoid injection attacks. Additionally, adopting those frameworks that securely handle data will reduce the chances of such security threats. Using libraries for input validation and avoiding direct concatenation of user data into queries will reduce such attacks drastically.
WAFs and intrusion detection systems can add an extra layer of protection by filtering and monitoring suspicious patterns. Injection vulnerabilities can be discovered early in their life cycle by frequent security audits, code reviews, and automated scanning so that teams can work on remediating them before they are vulnerable.
2. Cross-Site Scripting
XSS is a vulnerability that allows an attacker to inject malicious scripts into web pages viewed by other customers. These types of attacks allow session cookies to be stolen, user inputs to be captured, or even the defacement of websites. This threat commonly occurs when applications fail to sanitize or encode data being rendered onto web pages properly.
For example, encoding the outputs using Content Security Policy and using libraries that auto-sanitize data for developers will prevent XSS threats. For security testing, regularly using automated scanning tools and expert-level manual code reviews will help find the XSS vulnerabilities and fix the problems when application development is in an early stage.
SaC is a revolutionary approach, and it integrates security practices directly into the software development lifecycle (SDLC), treating security controls like any other part of the codebase. By integrating security checks directly into the code, security as code fosters a proactive security development culture that minimizes human errors and reduces detection-to-remediation time. It ensures security measures are implemented in an automated, consistent, and scalable way, and it will allow the developers to catch and mitigate the vulnerabilities early on in the process.
3. Broken Authentication and Session Management
Broken authentication is an attack where attackers get unauthorized access to several accounts because there are different weaknesses in the authentication ways, either due to weak passwords, unencrypted transport and storage, or poor session management. Poor session management may also enable active sessions to be hijacked by attackers.
To reduce this vulnerability, incorporate a robust password policy, use multi-factor authentication, and employ secure session handling techniques like timeouts and cookie security flags. Passwords should be stored using robust hashing algorithms, while regular auditing of authentication processes is highly recommended.
4. Security Misconfigurations

These are when the settings of security are not defined, maintained, or put in place to leave the application open to an attack. The configurations could include using default credentials, enabling unnecessary features, or setting improper permissions on cloud services.
Configuration guidelines should be followed to avoid security misconfiguration. This includes regularly updating software components and patching; automated tools should scan to find the misconfiguration. The principle of least privilege and periodic security review will also help in reducing the risk factors.
5. Insecure Deserialization
It happens when untrusted data is used for reconstituting objects, which results in successful attacks such as remote code execution, replay attacks, and privilege escalation. This is often not taken seriously, but the consequences it may cause are overwhelming since the attackers can change serialized data and then exploit processes that include deserialization.
Mitigating insecure deserialization requires developers to avoid deserializing data received from untrusted sources and use libraries that securely handle it. It can also be protected by input validation and the implementation of integrity checks, such as digital signatures on serialized objects.
6. Sensitive Data Exposure
Applications sometimes cannot adequately protect information, such as passwords, credit card numbers, or personal data, from falling into the wrong hands. It could result from poor encryption, bad key management, or failure to use HTTPS to bring data directly to the attackers.
Employ robust encryption algorithms. In addition, proper key management should be followed, and the usage of TLS for communication should be utilized, or the data could be exposed. Also, data masking and minimizing the storage of sensitive information can reduce the impact if an occurrence happens.
7. Cross-Site Request Forgery
This is one of those attack types whereby unauthorized commands are transmitted from a user whom the web application trusts. CSRF exploits a site’s trust in the user’s browser, enabling attackers to trick users into carrying out unwanted actions, like changing account details or initiating unwanted transactions without their consent.
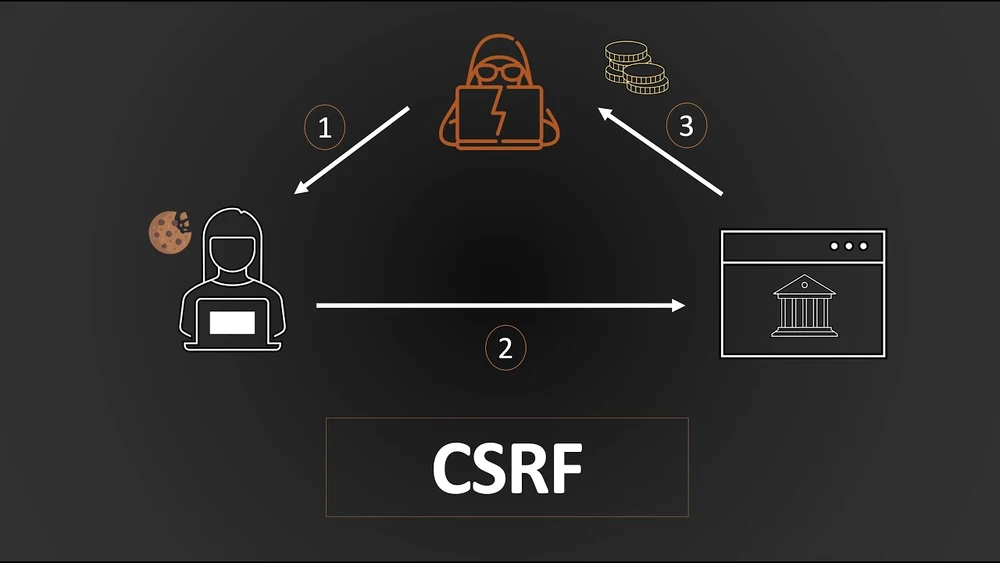
Avoid CSRF by introducing anti-CSRF tokens-unique, unpredictable values assigned to each user session. These tokens are embedded in forms and verified on the server side to ensure requests come from where they should. Furthermore, setting the SameSite cookie attribute prevents them from being delivered with cross-origin requests, significantly reducing the attack vectors for CSRF.
Developers’ confirmation of request headers, such as Origin and Referer, for assurance, should also come from trusted origins. It would be good if sensitive actions, like financial transactions or changing passwords, always required user confirmation through re-authentication or CAPTCHA. Performing regular automated security testing for CSRF issues and using secure coding practices are preventive measures themselves against these kinds of threats.
8. Using Components with Known Vulnerabilities
One of the very important aspects of software development is leveraging third-party libraries and frameworks to accelerate development. However, these components could introduce system vulnerabilities if they are not kept up-to-date.
Attackers frequently exploit known vulnerabilities in popular components to compromise applications. This can be mitigated by keeping all third-party components current, using tools that scan for known possible security threats, and regularly auditing the dependencies. Use version control and monitor advisories for updates to keep the software stack secure.
9. Improper Error Handling and Information Leakage
This may disclose sensitive information like stack traces, server details, or even database structures to the attacker. If error messages are too informative, they sometimes inadvertently help the attacker design more effective security threats against an application.
The developer should standardize the error-handling procedures so that no information leakage occurs, instead providing the end-user with generic error messages while securely logging a detailed error condition for internal review. It would further enable a central error management system to track issues and take remedial measures without actual exposure to sensitive information.
10. Insufficient Logging and Monitoring
These are two critical security threats that postpone the identification of malicious activities. Without proper logging, the developers could miss critical indicators of those security breaches and give attackers persistent latency. It sometimes leads to data loss, financial theft, and prolonged downtime.
Include comprehensive logging practices, real-time monitoring of system activities, and set up an alert mechanism for suspicious behavior. Employing SIEM systems will also be handy in incident analysis and response mechanisms.
Endnote On Security Threats
Software development security threats keep changing; hence, one needs to be quite vigilant and proactive on the developer’s side. You need to know the different security threats, from injection attacks to broken authentication, which will be the foundation for developing secure applications. Consider following the best practices for securing configurations, robust monitoring, and input validation.
Read more: Best Features & Key Functional Areas of Fintech Apps
Contact US | ThimPress:
Website: https://thimpress.com/
Fanpage: https://www.facebook.com/ThimPress
YouTube: https://www.youtube.com/c/ThimPressDesign
Twitter (X): https://x.com/thimpress_com